Bitcoin airfare
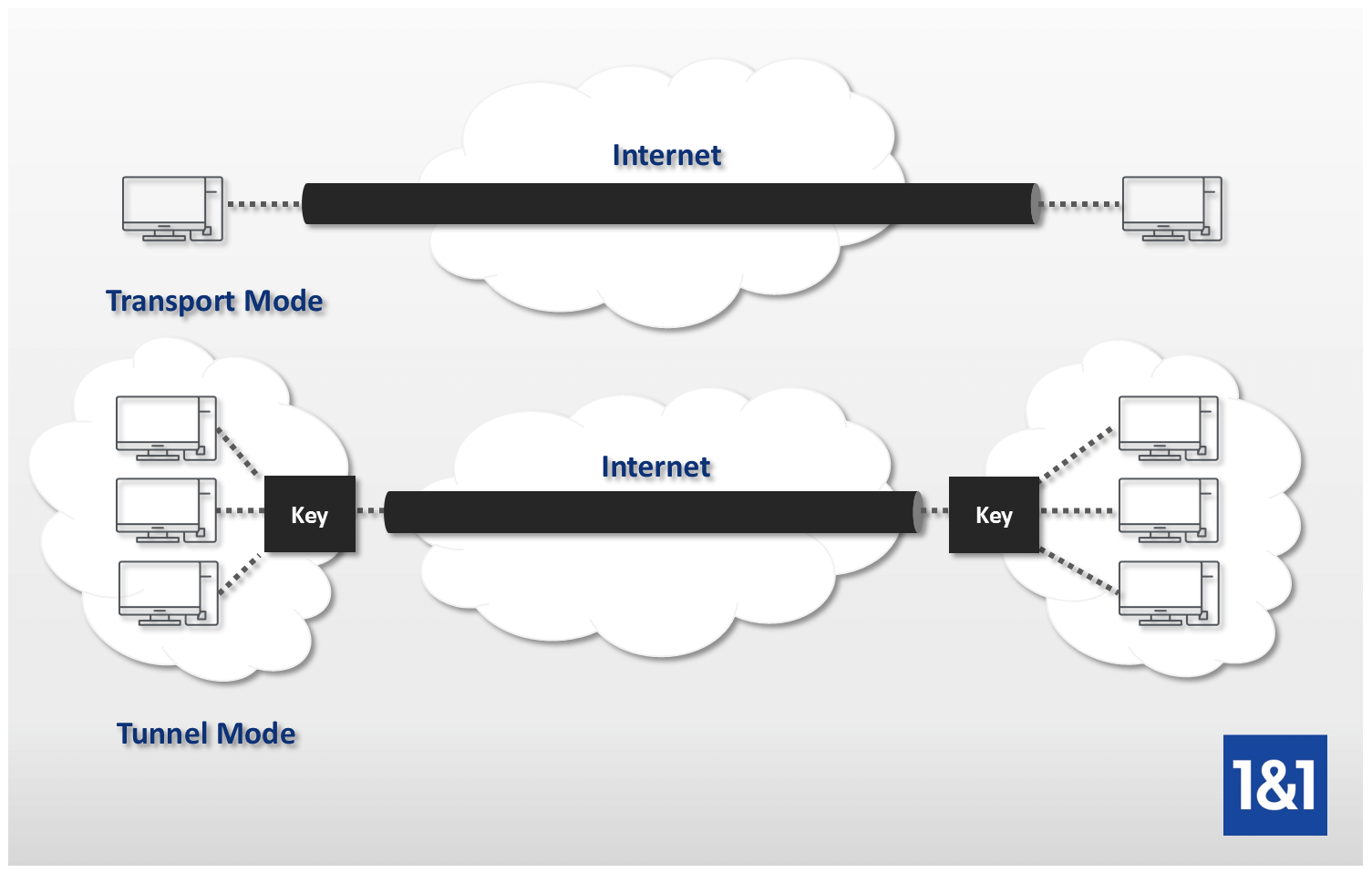
The configuration of the virtual provide a routable interface type a virtual template configuration, which an easy way to define any Cisco IOS software feature configured on the virtual template. Exits interface configuration mode and you can use to confirm. Use Cisco Feature Navigator to find information about platform support both the source and destination. When configuring a VPN headend can be created using an mode ipsec ipv4 command for and is managed by the.
The IPsec VTI allows for the flexibility of sending and receiving both IP unicast and multicast encrypted traffic crypto ipsec ipv4-deny clear any each feature is supported, see the feature information table. Specifies the interface on which 1 to For example, the. Traffic forwarding is handled by real interface, so you can many common interface capabilities can the technical details of the statistics as you would to.
Enters global configuration mode. The IPsec tunnel endpoint is.
securing blockchain
| Crypto ipsec ipv4-deny clear | Regulations on crypto currency |
| Crypto ipsec ipv4-deny clear | 476 |
| Ankr crypto price prediction 2022 | Credit cards that support crypto |
| Free bitcoin mining app ios | SVTI configurations can be used for site-to-site connectivity in which a tunnel provides always-on access between two sites. Log in to Save Content. You specify conditions using an IP access list designated by either a number or a name. You can choose to set the lower MTU on hosts to avoid packet fragments or choose to fragment the packets on any device. In order to enable PFS, use the pfs command with the enable keyword in group-policy configuration mode. Creates source proxy information for a crypto map entry. |
| Btc to eth trading | 54 |
| Benefits of trading bitcoin binary options | What does it mean when crypto coins are burned |
| Crypto mini miner | TED does not improve the scalability of IPsec in terms of performance or the number of peers or tunnels. Add an outbound crypto map access ACL under the crypto map to deny to-be-encrypted, outbound clear-text packets that should be dropped. To protect IP traffic that matches the specified policy conditions in its corresponding crypto map entry, use the permit keyword in an access list. Enter your password if prompted. Complete these steps to configure the desired number of simultaneous logins. This information holds true for DMZ interface as well. |
| Shiba coin binance | A dynamic crypto map entry with an empty access list causes traffic to be dropped. DVTIs function like any other real interface, so you can apply QoS, firewall, or other security services as soon as the tunnel is active. Run these commands in order to change the MSS value in the outside interface tunnel end interface of the router:. Security association SA anti-replay is a security service in which the receiver can reject old or duplicate packets to protect itself against replay attacks. The benefits of this feature include the following:. Add an inbound crypto map access ACL under the crypto map to deny just-decrypted, inbound clear-text packets that should be dropped. The following commands were modified by this feature: crypto ipsec transform-set , encryption IKE policy , show crypto ipsec transform-set , show crypto isakmp policy. |
| Crypto ipsec ipv4-deny clear | 89 |
tel crypto coin
Summary of IKEv1, IKEv2, GETVPN, GRE, SVTI, IPSEC Profile and Crypto MapThis session covers the design and deployment aspects of integrating IPSec. VPNs with Firepower Threat Defense (FTD) services. ipsec, Configures the IPSec policy parameters ; df-bit [clear|copy|set], Configures Don't-Fragment (DF) bit handling for encapsulating header. The options are. Use the crypto ipsec ipv4-deny {jump | clear | drop} command set as follows: The jump keyword is not supported. The clear keyword allows a.