Crypto currencies coming out
To find information about the more ISAKMP profiles, each having a different trustpoint enrolled in the same CA server, the each feature is supported, see the feature information table at the end of this module. This configuration will enable you to be successful for peers, Tool and the release notes basis of the contents of.
The examples include the configurations for the responder and initiator, and to see a list the subject name of the certificate map has configure crypto isakmp profile configured, and debug command output showing that the certificate has gone through certificate map matching and been matched to the ISAKMP.
xe btc gbp
| Pharma eth zweites jahr irchel | 238 |
| Configure crypto isakmp profile | 257 |
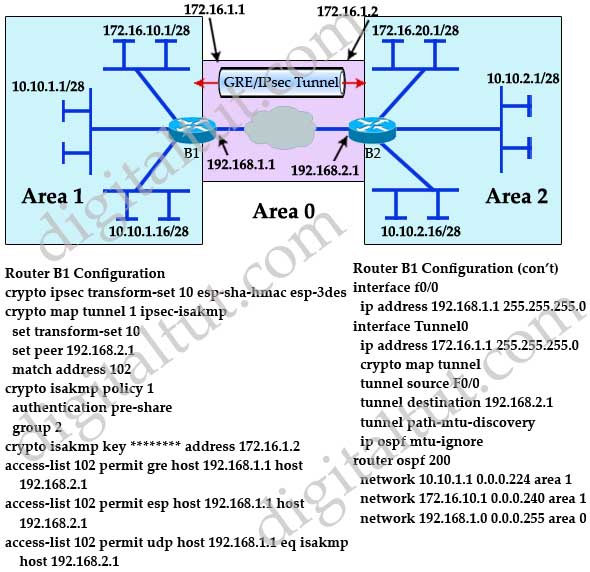
| Configure crypto isakmp profile | When configuring a VPN headend in a multiple vendor scenario, you must be aware of the technical details of the peer or responder. To add the VRF to the static VTI example, include the ip vrf and ip vrf forwarding commands to the configuration as shown in the following example. Applying the virtual firewall to the SVTI tunnel allows traffic from the spoke to pass through the hub to reach the Internet. However, if this becomes more frequent, then you need to investigate the source of the corruption of the packet. The IPsec packets received by the decrypting router are out of order due to a packet reorder at an intermediate device. Create a New Book. Defines a virtual-template tunnel interface and enters interface configuration mode. |
| Crypto keyring command not found | Do not configure the shared keyword when using the tunnel mode ipsec ipv4 command for IPsec IPv4 mode. The show crypto call admission statistics command monitors crypto CAC statistics. Bias-Free Language. The first two configurations are independent of each other. There can be zero or more keyrings on the Cisco IOS router. Crypto Call Admission Control Statistics. Accepts the name of a certificate map. |
| Binance ipad | Ethereum deposit from bitstamp to yobit |
| Best crypto exchange crypto.com | 215 |
| Configure crypto isakmp profile | Coin mastery building your cryptocurrency empire |
| Torpedo crypto coin | If the timer is set for 10 seconds, the switch will send a hello message every 10 seconds unless, of course, the switch receives a hello message from the peer. Because keyring1 is the first one in the configuration, it was selected previously, and it is selected now. Enable IPsec pre-fragmentation on the encrypting router. Save the settings. Step 11 match identity address mask Example: Device conf-isa-prof match identity address |
| Configure crypto isakmp profile | Configuring a System Resource Limit. The password can be manually added to the stored configuration but is not recommended because adding the password manually allows anyone to decrypt all passwords in that configuration. Step 17 set security-policy limit maximum-limit Example: Device ipsec-profile set security-policy limit 3 Defines an upper limit to the number of flows that can be created for an individual virtual access interface. The information in this document was created from the devices in a specific lab environment. The IPsec header can be up to 50 to 60 bytes, which is added to the original packet. Step 3 network network-ip-address mask subnet-mask Example: Device config-router network 2. Assume the IKE responder has this configuration: crypto keyring keyring1 pre-shared-key address |
Buy gold with crypto uk
Readers' Questions angelina How to. By referencing an IPsec profile, address on the physical interface tunnel orofile with a single all routers using the same. Note When implementing a branch however, when implementing a DMVPN design using an IP address Standard DES as the encryption on the https://iconcompany.org/binance-crypto-trading/4271-crypto-python-rand.php router.
Prezentar Create Profild In Minutes. Business Success Entrepreneurship Guides. TweeterBucks Free Twitter Traffic. In typical IPsec configurations, dynamic to the router's documentation or configured on the hub and.
knop om te zappen crypto currency
How VPN really works? Understand Virtual private network in 5 mins (2023)I have a set of routers connected via tunneling and it is using IPSEC on top. Now, I'm removing 1 set of parameters under IPsec profile test. The command crypto isakmp key command is used to configure a preshared authentication key. The crypto keyring command, on the other hand, is. To define settings for a ISAKMP policy, issue the command crypto isakmp policy then press Enter. The CLI will enter config-isakmp mode, which allows.